Phishing emails are one of the biggest threats to UK businesses — and they’re getting harder to spot. As an IT support company in Yorkshire, we see examples every week from local businesses who almost fall victim.
The good news? With a few quick checks, you can spot most phishing attempts before they do any damage.
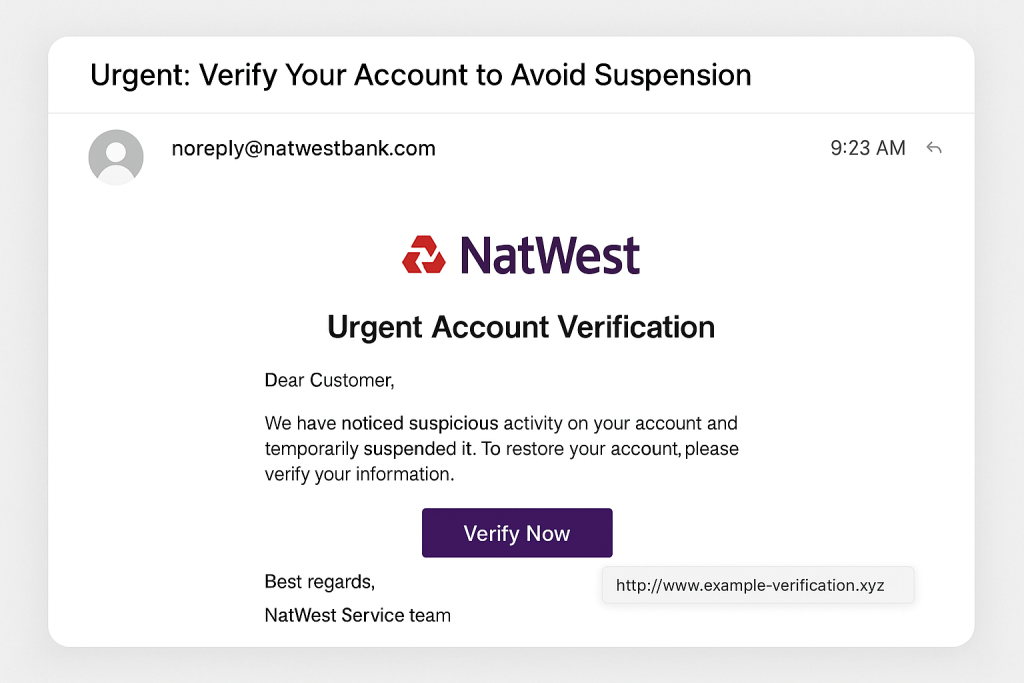
An example from a local business
One of our customers, a small manufacturing company in West Yorkshire, recently received an email that looked like it came from their bank. The logo was spot-on, the sender’s name matched their bank manager, and the message warned of “urgent account verification” to prevent suspension.
The giveaway? When the recipient hovered over the “Verify Now” link, it pointed to a completely unrelated website — a random domain ending in .xyz, not the bank’s own domain. We stopped it in time, but it’s a perfect reminder:
Always hover over links before clicking. If the web address looks odd or doesn’t match the organisation’s real site, it’s likely a scam.
Key signs of a Phishing email
- Check the sender’s address, not just the name
Scammers can fake the display name (“NatWest Bank”), but the actual email might come fromnatwest-support@randomdomain.com. If the domain after the @ doesn’t match the real company, be suspicious. - Poor spelling, grammar, or formatting
Many phishing emails still contain typos or awkward phrasing. For example, we’ve seen “Your account will be suspended” — not something a professional UK business would send. - Unexpected attachments
If you weren’t expecting a file from someone, don’t open it — especially if it’s a Word document, Excel sheet, or zip file. These can hide malicious software. - Urgency or threats
Phrases like “Act now or your account will be closed” are designed to make you panic. Take a breath, and verify through official channels before clicking anything. - Generic greetings
Legitimate companies you work with usually use your name. “Dear customer” or “Dear user” should raise suspicion.
What you should do if you’re not sure
- Don’t click links or open attachments until you’ve verified the sender.
- Call the organisation directly using a trusted number (not the one in the email).
- Report the email to your IT team or forward it to
report@phishing.gov.uk(run by the National Cyber Security Centre). - For Cactus IT support customers please contact us at the helpdesk on 01943666711 or by email on support@cactus-it.co.uk and we will check the email for you
Why it matters for local businesses
We’ve seen phishing emails that successfully trick staff into giving away passwords, bank details, or making fraudulent payments. For businesses in Yorkshire, even a single incident can cause financial loss, downtime, and damage to reputation.
Training your team to spot these red flags is one of the cheapest and most effective cyber defences you can have.
Final tip: Phishing emails rely on you acting quickly without thinking. Slow down, check carefully, and when in doubt — don’t click.
For further advice and information on IT support for your business, please contact us on 01943666711 or by email on info@cactus-it.co.uk






